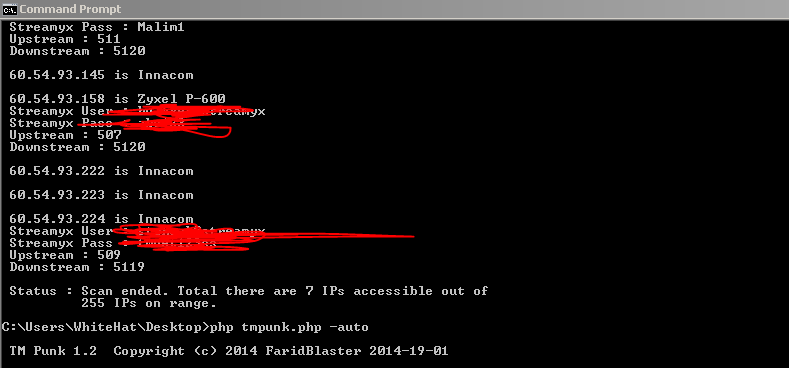
Janji-janji kemenangan yang pasti buat para pendokong kebenaran....!
Janji-janji kemenangan yang pasti buat para pendokong kebenaran....!
Janji kemenangan untuk Haq.
Bencana yang melanda bumi Palestin bukanlah ke atas Palestin sahaja tetapi terhadap umat Islam keseluruhannya.
Dan sesungguhnya yahudi langsung tidak ada hak ke atas bumi Palestin samada berdasarkan hujah sejarah atau agama (ia tetap milik umat Islam).
Dan sesungguhnya umat Islam akan menang di Palestin kerana adalah satu perkara yang mustahil menangnya kelompok batil ke atas golongan haq.
Syiekh Dr Yusuf Al-Qardawi

Sumber dari : https://www.facebook.com/AmanPalestinOfficial/posts/758829027491939
Bencana yang melanda bumi Palestin bukanlah ke atas Palestin sahaja tetapi terhadap umat Islam keseluruhannya.
Dan sesungguhnya yahudi langsung tidak ada hak ke atas bumi Palestin samada berdasarkan hujah sejarah atau agama (ia tetap milik umat Islam).
Dan sesungguhnya umat Islam akan menang di Palestin kerana adalah satu perkara yang mustahil menangnya kelompok batil ke atas golongan haq.
Syiekh Dr Yusuf Al-Qardawi

Sumber dari : https://www.facebook.com/AmanPalestinOfficial/posts/758829027491939
Ugut Terjun Dari Jejambat PLUS Sebab Bergaduh Dengan Pakwe
Macam macam hal yang terjadi sekarang. Terbaru, hanya kerana berselisih faham dengan teman lelaki, seorang wanita bertindak memanjat papan iklan gergasi pada jejambat di Lebuhraya Utara- Selatan (Plus) berhampiran tol Jelapang, Bandar Meru Raya di sini dan mengugut untuk terjun.
Bagaimanapun, wanita itu membatalkan niatnya itu selepas berjaya dipujuk oleh anggota bomba dan penyelamat.
Ketua Balai Bomba dan Penyelamat Meru, Norazlina Robak’aee berkata, lima anggota bergegas ke lokasi kejadian setelah menerima panggilan pada jam 6.48 petang dan mendapati seorang wanita berusia awal 30-an duduk di atas papan iklan berkenaan.
“Wanita yang dipercayai warga Thailand itu hanya pakai baju tanpa lengan dan berseluar pendek. Dia menangis sambil menjerit memarahi teman lelakinya yang turut berada di tempat kejadian.
“Ketika dipujuk, wanita berkenaan bertindak berdiri dan sekali sekala mengugut mahu terjun dari papan iklan terbabit dengan banyak kenderaan lalu lalang di bawah jejambat berkenaan,”
Beliau berkata, pada mulanya pihaknya sukar meminta mangsa turun daripada papan iklan tersebut kerana emosinya yang tidak stabil namun selepas sejam dia berjaya ditenangkan.
“Selepas hampir sejam, akhirnya kita berjaya menenangkannya dan berjaya membawa turun mangsa dari papan iklan terbabit.
“Mangsa diserahkan kepada pihak polis dan dihantar UNTUK mendapatkan rawatan di Hospital Raja Permaisuri Bainun,” katanya. – Sinar Harian
Netstat tips and tricks for Windows Server admins
Maintaining command-line finesse is an important objective for Windows Server administrators. Rick Vanover offers some pointers on using the netstat command.
Netstat is a command that some Windows Server admins use every day, while others only use it when there is a problem. I fall into the latter category; I use netstat as a diagnosis tool when something has gone awry, or when I am trying to track something down.
The 10 parameters to the Windows netstat command can display scores of additional information for troubleshooting or everyday use. The most common iteration of netstat is to use the -a parameter, which displays all connections and listening ports. However, netstat displays useful information even without parameters. Here are some pointers on using the netstatcommand:
Fully qualified domain name: The -f parameter will display the fully qualified domain name (FQDN) of the foreign address in the netstat display. This will resolve names internally and externally if possible. Figure A shows the FQDN resolution within netstat. Figure A
What process is running on the open port: Tracking down which process identifier (PID) has a port open is quite easy when netstat is run with the -a -n -o combination of parameters. Read my Windows Server 2008 tip on this sequence of commands, and see it in action in Figure B.Figure B
You can take this one step further with the implementation of friendly names for each process with the -b netstat parameter. This parameter requires administrative permissions and is shown in Figure C. Figure C
Note that the remote addresses pointing to the 192.168.1.220:3261 address are the Windows iSCSI initiator service and display differently than the other services listed.
Display routing table: If you need to determine why one system has a different experience than another on the same network, netstat can display a route of the current system with the -rparameter. Figure D shows this in use (note the persistent routes section that would display any static routes added to the Windows Server). Figure D
These four netstat commands can greatly add to the troubleshooting efforts for Windows administrators. How else do you use netstat? Share your tips in the discussion.
ipconfig
ipconfig is a commmand line utility available on all versions of Microsoft Windows starting with Windows NT. ipconfig is designed to be run from the Windows command prompt. This utility allows you to get the IP address information of a Windows computer. It also allows some control over active TCP/IP connections. ipconfig is an alternative to the older 'winipcfg' utility.
ipconfig Usage
From the command prompt, type 'ipconfig' to run the utility with default options. The output of the default command contains the IP address, network mask and gateway for all physical and virtual network adapters.
'ipconfig' supports several command line options as described below. The command "ipconfig /?" displays the set of available options.
ipconfig /all
This option displays the same IP addressing information for each adapter as the default option. Additionally, it displays DNS and WINS settings for each adapter.ipconfig /release
This option terminates any active TCP/IP connections on all network adapters and releases those IP addresses for use by other applications. 'ipconfig /release" can be used with specific Windows connection names. In this case, the command will affect only the specified connections and not all. The command accepts either full connection names or wildcard names. Examples:- ipconfig /release "Local Area Connection 1"
ipconfig /release *Local*
ipconfig /renew
This option re-establishes TCP/IP connections on all network adapters. As with the release option, ipconfig /renew takes an optional connection name specifier.
Both /renew and /release options only work on clients configured for dynamic (DHCP) addressing.
Note: The remaining options below are only available on Windows 2000 and newer versions of Windows.
ipconfig /showclassid, ipconfig /setclassid
These options manage DHCP class identifiers. DHCP classes can be defined by administrators on a DHCP server to apply different network settings to different types of clients. This is an advanced feature of DHCP typically used in business networks, not home networks.ipconfig /displaydns, ipconfig /flushdns
These options access a local DNS cache that Windows maintains. The /displaydns option prints the contents of the cache, and the /flushdns option erases the contents.
This DNS cache contains a list of remote server names and the IP addresses (if any) they correspond to. Entries in this cache come from DNS lookups that happen when attempting to visit Web sites, named FTP servers, and other remote hosts. Windows uses this cache to improve the performance of Internet Explorer and other Web-based applications.
In home networking, these DNS options are sometimes useful for advanced troubleshooting. If the information in your DNS cache becomes corrupted or outdated, you could face difficulty accessing certain sites on the Internet. Consider these two scenarios:
- The IP address of a Web site, email server or other server changes (rare occurence). The name and address of this site normally stay in your cache for 24 hours after your last visit. You may need to clear your cache to access the server sooner.
- A Web site or other server was offline when you last visited it (hopefully a rare occurence) but since has come back online. The cache will normally keep a record that the server is offline for 5 minutes afer your last visit. You may need to clear your cache to access the server sooner.
ipconfig /registerdns
Similar to the above options, this option updates DNS settings on the Windows computer. Instead of merely accessing the local DNS cache, however, this option initiates communication with both the DNS server (and the DHCP server) to re-register with them.
This option is useful in troubleshooting problems involving connection with the Internet service provider, such as failure to obtain a dynamic IP address or failure to connect to the ISP DNS server.
Like the /release and /renew options, /registerdns optionally takes the name(s) of specific adapters to update. If no name parameter is specified, /registerdns updates all adapter
Basic Telnet Tutorial
Telnet was developed in 1969 to aid in remote connectivity between computers over a network. Telnet can connect to a remote machine that on a network and is port listening. Most common ports to which one can connect to through telnet are:
Port 21 - File Transfer Protocol
Port 22 - SSH Remote Login Protocol
Port 23 - Telnet Server
Port 25 - Simple Mail Transfer Protocol (SMTP)
Port 53 - Domain Name Server (DNS)
Port 69 - Trivial File Transfer Protocol (TFTP)
Port 70 - Gopher
Port 21 - File Transfer Protocol
Port 22 - SSH Remote Login Protocol
Port 23 - Telnet Server
Port 25 - Simple Mail Transfer Protocol (SMTP)
Port 53 - Domain Name Server (DNS)
Port 69 - Trivial File Transfer Protocol (TFTP)
Port 70 - Gopher
Port 80 - Hyper Text Transfer Protocol (HTTP)
Port 110 - Post Office Protocol 3 (POP3)
Telnet can be used to connect to virtually any machine that listens on ports. In other words, you can connect to any machine that has certain ports open. Once connected to a machine, you need to issue unix based commands to interact with the remote service. For example, a user don't need to login, check and send mails only through his email service provider's interface but this can be achieved using simple telnet commands. It is because of this reason that many hackers can send spoofed emails or access information such as which services are running on the remote machine. This is also called banner grabbing or daemon tracking. Black hat hackers can also use telnet to sniff network packets which might contain sensitive information such as usernames and passwords. This is achieved by using telnet and network utilities such as tcpdump and wireshark.
Telnet client and server functionality comes built-in in most operating systems. However, there are several third-party applications like putty client that enable remote connectivity. A user can connect to a remote machine through several access modes such as raw access, SSH access, etc. SSH mode offers encryption and security and hence can prevent eavesdropping by hackers. This is by far the most secure way of connecting to a machine. However, it is necessary that the remote machine supports SSH login to make use of the encryption and security features.
On windows machines, telnet client can simply be started by issuing the telnet command in windows command shell. The following example would help you connect to a remote machine on the HTTP Port 80 and issue a GET command which would fetch a file as your web browser does it behind scenes:
Command Prompt> Telnet
Command Prompt> open (somedomain.com or ip address) 80
At this stage, you would be connected to somedomain.com or ip address on port 80 and the daemon that is running on port 80 (most probably HTTP Server) would be waiting for HTTP requests.
GET / HTTP/1.1
host: somedomain.com (or ip address)
Port 110 - Post Office Protocol 3 (POP3)
Telnet can be used to connect to virtually any machine that listens on ports. In other words, you can connect to any machine that has certain ports open. Once connected to a machine, you need to issue unix based commands to interact with the remote service. For example, a user don't need to login, check and send mails only through his email service provider's interface but this can be achieved using simple telnet commands. It is because of this reason that many hackers can send spoofed emails or access information such as which services are running on the remote machine. This is also called banner grabbing or daemon tracking. Black hat hackers can also use telnet to sniff network packets which might contain sensitive information such as usernames and passwords. This is achieved by using telnet and network utilities such as tcpdump and wireshark.
Telnet client and server functionality comes built-in in most operating systems. However, there are several third-party applications like putty client that enable remote connectivity. A user can connect to a remote machine through several access modes such as raw access, SSH access, etc. SSH mode offers encryption and security and hence can prevent eavesdropping by hackers. This is by far the most secure way of connecting to a machine. However, it is necessary that the remote machine supports SSH login to make use of the encryption and security features.
On windows machines, telnet client can simply be started by issuing the telnet command in windows command shell. The following example would help you connect to a remote machine on the HTTP Port 80 and issue a GET command which would fetch a file as your web browser does it behind scenes:
Command Prompt> Telnet
Command Prompt> open (somedomain.com or ip address) 80
At this stage, you would be connected to somedomain.com or ip address on port 80 and the daemon that is running on port 80 (most probably HTTP Server) would be waiting for HTTP requests.
GET / HTTP/1.1
host: somedomain.com (or ip address)
Issuing the command above would make the HTTP Server return the file requested, in this case it would be the default file at the root location. You can find some additional basic telnet commands at the Microsoft Technet library -http://technet.microsoft.com/en-us/library/c.aspx
Most applications and embedded devices make use of the telnet technology to connect to remote server machines and provide end user functionality. The most common use of telnet stands to enable remote authentication and access.
Resepi Biskut Aiskrim Strawberry
Bahan-Bahan
260 gm butter
120 gm gula icing
320 gm tepung gandum
60 gm tepung jagung
40 gm tepung ubi
1/2 sudu teh baking powder
40 gm serbuk badam
Sdkt vanilla essence
2 sudu teh strawberry emulco
sedikit pewarna pink/merah
1 biji kuning telur utk sapu atas biskut
Topping coklat dan manik2/bunga sebagai hiasan
Cara-Caranya
- Pukul butter dan gula sehingga kembang.
- Kemudian campurkan tepung-tepung yang telah diayak bersama baking powder dan juga serbuk badam. - - Gaul rata sehingga menjadi doh.
- Canai doh dan kemudian gelek dan terap dengan acuan ais krim.
- Atur diatas loyang pembakar. Sapukan telur diatas biskut dan bakar pada suhu 150 degree selama 25 minit atau sehingga ia masak.
- Biarkan biskut benar2 sejuk, barulah celup dngn coklat cair.
- Celup hujung biskut dengan coklat dan tabur manik berwarna diatas coklat tersebut.
= Hias biskut ikut creativiti anda.
260 gm butter
120 gm gula icing
320 gm tepung gandum
60 gm tepung jagung
40 gm tepung ubi
1/2 sudu teh baking powder
40 gm serbuk badam
Sdkt vanilla essence
2 sudu teh strawberry emulco
sedikit pewarna pink/merah
1 biji kuning telur utk sapu atas biskut
Topping coklat dan manik2/bunga sebagai hiasan
Cara-Caranya
- Pukul butter dan gula sehingga kembang.
- Kemudian campurkan tepung-tepung yang telah diayak bersama baking powder dan juga serbuk badam. - - Gaul rata sehingga menjadi doh.
- Canai doh dan kemudian gelek dan terap dengan acuan ais krim.
- Atur diatas loyang pembakar. Sapukan telur diatas biskut dan bakar pada suhu 150 degree selama 25 minit atau sehingga ia masak.
- Biarkan biskut benar2 sejuk, barulah celup dngn coklat cair.
- Celup hujung biskut dengan coklat dan tabur manik berwarna diatas coklat tersebut.
= Hias biskut ikut creativiti anda.
Resepi Biskut Aiskrim Nestum
Resepi Biskut Aiskrim Nestum
Bahan-bahan:
200 gm tepung gandum
70 gm tepung kastad
160 gm nestum (Boleh kisar nestum ni)
75 gm gula halus
180 gm butter
1 biji telur
1/2 tsp serbuk penaik
Bahan hiasan:
250 gm coklat masakan (Cairkan secara double boiler)
Gula manik atau apa-apa hiasan yang sesuai
Cara-cara:
- Ayak tepung gandum, tepung kastad dan serbuk penaik. Kemudian satukan dengan nestum.
- Dalam satu mangkuk lain, putar butter dan gula hingga gebu dan warna menjadi pucat.
- Masukkan telur dan pukul rata.
- Masukkan bahan ayak dan uli hingga menjadi doh.
- Canai dan terap dengan acuan bentuk aiskrim.
- Bakar dalam oven pada suhu 160 C sehingga biskut masak. Sejukkan di atas redai.
- Celupkan hujung biskut ke dalam coklat yang telah dicairkan dan taburkan gula hiasan di atasnya.
- Setelah coklat mengeras, simpan biskut di dalam bekas kedap udara.
Bahan-bahan:
200 gm tepung gandum
70 gm tepung kastad
160 gm nestum (Boleh kisar nestum ni)
75 gm gula halus
180 gm butter
1 biji telur
1/2 tsp serbuk penaik
Bahan hiasan:
250 gm coklat masakan (Cairkan secara double boiler)
Gula manik atau apa-apa hiasan yang sesuai
Cara-cara:
- Ayak tepung gandum, tepung kastad dan serbuk penaik. Kemudian satukan dengan nestum.
- Dalam satu mangkuk lain, putar butter dan gula hingga gebu dan warna menjadi pucat.
- Masukkan telur dan pukul rata.
- Masukkan bahan ayak dan uli hingga menjadi doh.
- Canai dan terap dengan acuan bentuk aiskrim.
- Bakar dalam oven pada suhu 160 C sehingga biskut masak. Sejukkan di atas redai.
- Celupkan hujung biskut ke dalam coklat yang telah dicairkan dan taburkan gula hiasan di atasnya.
- Setelah coklat mengeras, simpan biskut di dalam bekas kedap udara.
Resepi Biskut Daisy
Bahan-Bahan:
Bahan topping:
160 gm mentega
160 gm tepung gandum
60 gm gula aising
60 gm tepung gandum
2 sudu kecil pes strawberi 250 gm mentega
60 gm gula aising
220 gm tepung gandum
240 gm tepung jagung
1 sudu kecil esen vanila
Cara:
1. Pukul mentega dan gula hingga kembang.
2. Masukkan tepung dan gaul sebati hingga manjadi doh. Canai dan terap.
3. Untuk topping, pukul mentega dan gula hingga sebati.
4. Masukkan pes strawberi dan tepung.
5. Uli hingga menjadi doh lembut.
6. Masukkan ke dalam nozel dan picitkan ke atas doh yang sudah diterap tadi.
Resepi Biskut Ferrero Rocher
BISKUT FERRERO ROCHER
Bahan-bahan:
250gm butter
80gm gula icing
20gm qroquant/cornfleks hancur
360gm tpg gandum
100gm almond powder
40gm tpg jagung
1/2 sdt esen vanilla
almond nibs secukupnya (utk menyalut biskut)
3bj putih telur (utk melekatkan almond nibs dgn biskut)
coklat masakan secukupnya.(utk menyalut biskut)
Cara-cara:
-putar butter & gula sebati.masukkan qroquant.
-masukkan esen vanilla.
-masukkan tpg gandum,almond powder & tpg jagung. uli sebati.
-panaskan oven suhu 150c.
-bulatkan adunan mengikut saiz yg dikehendaki.letakkan dlm dulang pembakar yg sudah dilengser dgn marjerin.
-bakar suhu 150c selama 20-25 minit.
-golekkan biskut yg telah dibakar ke dalam telur putih.kemudian golekkan di atas almond nibs.
-bakar balik biskut lebih kurang 5 minit.
-cairkan coklat masakan & golekkan biskut dlm coklat & masukkan ke dlm paper cup.biarkan sejuk & siap utk dihidang...;)
SELAMAT MENCUBA!..;)
Resepi Kek Coklat Moist Kukus Cara Mudah
Resepi Kek Coklat
1 cawan serbuk coklat
1 cawan gula
1 cawan minyak masak (boleh ganti dengan buttercup)
1 1/2 cawan tepung gandum
1 tin susu cair
1 1/2 sudu kecil soda bikabonat
1 1/2 sudu kecil serbuk penaik
2 biji telur
1 cawan gula
1 cawan minyak masak (boleh ganti dengan buttercup)
1 1/2 cawan tepung gandum
1 tin susu cair
1 1/2 sudu kecil soda bikabonat
1 1/2 sudu kecil serbuk penaik
2 biji telur
Hiasan Kek
1 bar coklat masakan
Coklat rice/atau apa-apa hiasan yang menarik untuk kek
Coklat rice/atau apa-apa hiasan yang menarik untuk kek
Cara-cara masakan;
1) Sebelum kita bancuh bahan-bahan, didihkan air didalam alat kukusan.
2) Sementara tunggu air mendidih, kita mulai adunan dengan ambil 2 biji telur dan dipukul sehingga kembang.
2) Coklat, gandum, gula, serbuk penaik dan soda bikarbonat digaul sekali.
3) Susu cair dan minyak masak dicampur ke dalam telur yang telah dipukul sehingga kembang.
4) Campur adunan di dalam langkah 2 ke dalam langkah 3.
5) Kacau sehingga sebati.
7) Sediakan loyang kek yang sudah disapu dengan majerin dan masukkan adunan kek yang sudah sebati.
8 ) Kukus sehingga masak kira-kira 45 minit. (tempoh masa kek siap masak bergantung kepada saiz loyang kek dan saiz api yang digunakan tapi sebaiknya pantau pada masa 30 minit)
*untuk cek masak ke tak kek ini boleh cek dengan cucuk kek menggunakan lidi. kalau takde apa yang melekat pada lidi bermakna kek tue dah masak.
9) Selepas masak, cairkan bar coklat dan sapu di atas dan sekeliling kek.
10) Letakkan hiasan dan masukkan ke dalam peti sejuk untuk keraskan coklat hiasan.
2) Sementara tunggu air mendidih, kita mulai adunan dengan ambil 2 biji telur dan dipukul sehingga kembang.
2) Coklat, gandum, gula, serbuk penaik dan soda bikarbonat digaul sekali.
3) Susu cair dan minyak masak dicampur ke dalam telur yang telah dipukul sehingga kembang.
4) Campur adunan di dalam langkah 2 ke dalam langkah 3.
5) Kacau sehingga sebati.
7) Sediakan loyang kek yang sudah disapu dengan majerin dan masukkan adunan kek yang sudah sebati.
8 ) Kukus sehingga masak kira-kira 45 minit. (tempoh masa kek siap masak bergantung kepada saiz loyang kek dan saiz api yang digunakan tapi sebaiknya pantau pada masa 30 minit)
*untuk cek masak ke tak kek ini boleh cek dengan cucuk kek menggunakan lidi. kalau takde apa yang melekat pada lidi bermakna kek tue dah masak.
9) Selepas masak, cairkan bar coklat dan sapu di atas dan sekeliling kek.
10) Letakkan hiasan dan masukkan ke dalam peti sejuk untuk keraskan coklat hiasan.
BUAT DUIT DENGAN HANYA BEKERJA DIRUMAH SAHAJA
Jobdirumah ini adalah sebuah websites yang memberi latihan dengan tawaran kerja-kerja jenis pekerjaan freelance yang bertanggungjawab untuk mengumpul maklumat dari internet, memasukkan maklumat ke dalam sistem, membuat kajian maklumat yang dikumpul, menyediakan laporan dan kerja-karja am yang berkaitan.
Setelah anda mengikuti program latihan bekerja dirumah ini, anda boleh mendapat 2 pendapatan sampingan:
A. Dengan menjadi freelance
- Anda bekerja dengan majikan antarabangsa. Siapkan projek yang diberikan oleh majikan. Setelah majikan berpuas hati dengan hasil kerja anda, majikan akan memberikan anda bayaran yang telah dijanjikan dalam USD (3 kali ganda dari wang Malaysia).
- Kerja anda mudah sahaja. Anda akan diberikan ID untuk melakukan promosi website Jobdirumah. Jika ada yang menyertai, anda akan dibayar melalui bank Malaysia pada hari Isnin-Jumaat.
Antara tugasan yang perlu anda lakukan ialah :
- Data Entry
- Menaip Dokumen
- Mengumpul Maklumat
- Menulis Artikal
- Menulis Laporan
- Khidmat Pelanggan
- Pembantu Maya
- Tugas Perkeranian
- Dan banyak lagi....
Anda risau ianya scam ?? Jangan bimbang, Jobdirumah terbukti membayar para freelancer seperti anda dan terdapat banyak review positif terhadap laman Jobdirumah.
Yuran pendaftaran cuma RM50 seumur hidup, namun pulangannya hampir setiap hari! Sekiranya anda berminat sila layari laman dibawah sekarang.
Hacking Using SqlMap
Install SQLMAP di Windows XP , 7 , 8
Selamat malam reader :)
Sekarang ini saya mau share tentang SQLMAP di windows.. Sebenernya main SQLMAP di windows ini emang agak ribet.. Dari mulai mendownload Python , active python dan yg terakhir mendownlaoad SQLMAP nya..
Untuk command SQLMAP di windows dengan di Linux tetep sama kok, jadi gak perlu khawatir...
Oke langsung saja,
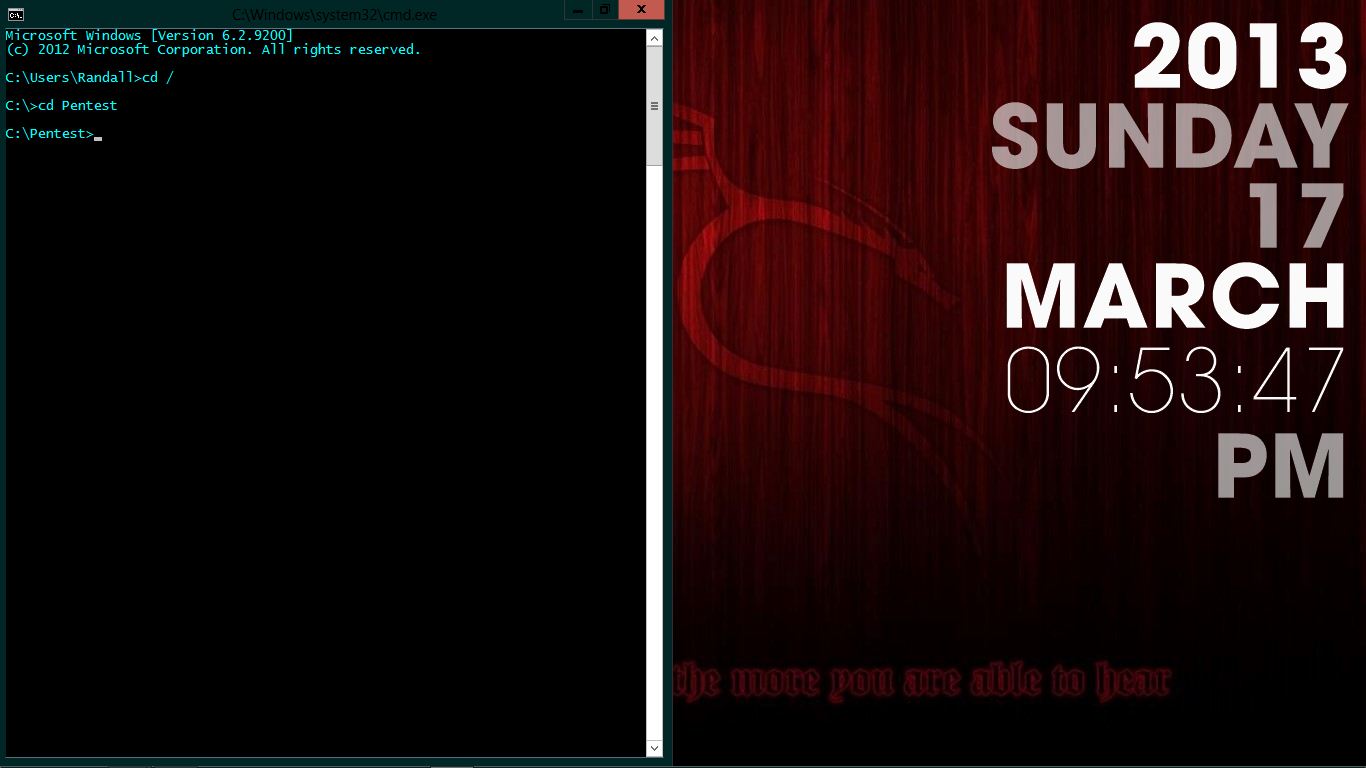
Extract SQLMAP nya di directory mana saja..
Dan cara untuk menggunakan SQLMAP nya adalah dengan membuka CMD dan masuk ke dalam directory dimana agan agan menyimpan SQLMAP
Contoh : Saya menyimpan SQLMAP di directory C:/ --> Pentest --> SQLMAP
SQLMAP berjalan =))
Sekian dari saya..
Semoga bermanfaat :)
Sekarang ini saya mau share tentang SQLMAP di windows.. Sebenernya main SQLMAP di windows ini emang agak ribet.. Dari mulai mendownload Python , active python dan yg terakhir mendownlaoad SQLMAP nya..
Untuk command SQLMAP di windows dengan di Linux tetep sama kok, jadi gak perlu khawatir...
Oke langsung saja,
- Download python, dan yg pasti buat windows.. download versi yg berapa saja..Download pyhton disini ..
- Download Active Python , agar SQLMAP dapat berjalan Download Active Python
- Dan yg terakhir download SLQMAP .. Download SQLMAP disini
Extract SQLMAP nya di directory mana saja..
Dan cara untuk menggunakan SQLMAP nya adalah dengan membuka CMD dan masuk ke dalam directory dimana agan agan menyimpan SQLMAP
Contoh : Saya menyimpan SQLMAP di directory C:/ --> Pentest --> SQLMAP
SQLMAP berjalan =))
Sekian dari saya..
Semoga bermanfaat :)